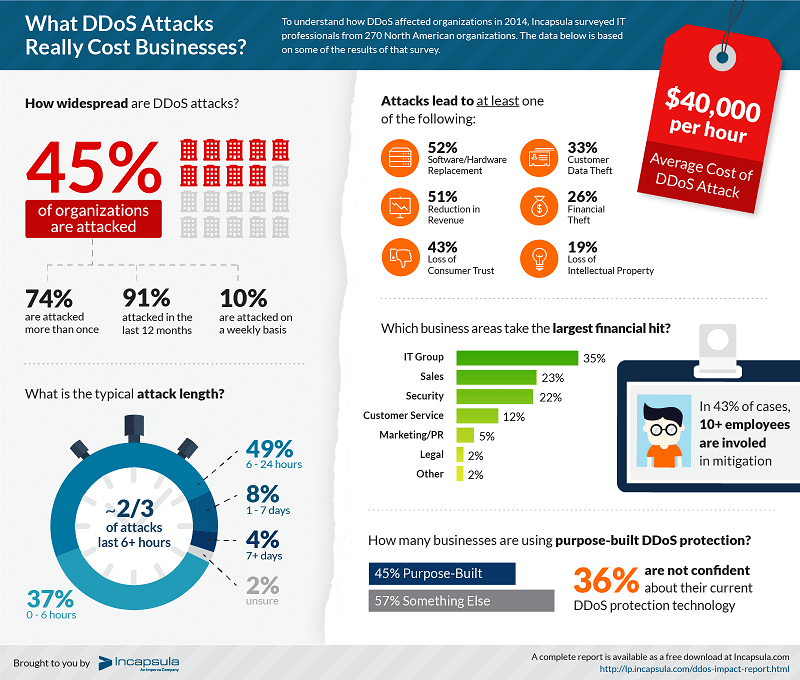
DDoS attacks are among the worst threats of recent years. According to research conducted by Incapsula a single attack can cost a company an average of $40,000 per hour and recent studies indicate that almost 75 percent of organizations have suffered at least one DDoS attack over the past 12 months.
The threats are the so-called DDoS attacks, which stands for Distributed Denial-of-Service.
Table of Contents
What is a DoS Attack
To understand what is a DDoS attack, it’s necessary, first of all, to analyze the DoS attacks. Acronym for Denial-of-Service, a DoS attack is a deliberate action that aims to saturate the resources of a computer system that provides a service to the client connected to it.
In network area, a DoS attack has targets such as servers, networks distribution or data center and acts so that their client – whether they are websites or visitors- have difficulties or are unable to reach them.
What is a DDoS Attack
A Distributed Denial-of-Service has the same purposes (disrupt communications between two or more nodes of the network) and the same targets (servers, data centers, distribution centers, etc.) but it takes on a much larger scale.
The lines of attack are varied (distributed in the network, in fact), and the strategy used is much more effective. By sending false requests for access to online resources targeted by more than one node, you have a greater chance that the attack will successful end in a shorter timeframe.
Since a DDoS attack needs a great synchronism, it is likely to be carried out by a small number of hackers who controls one or more botnets.
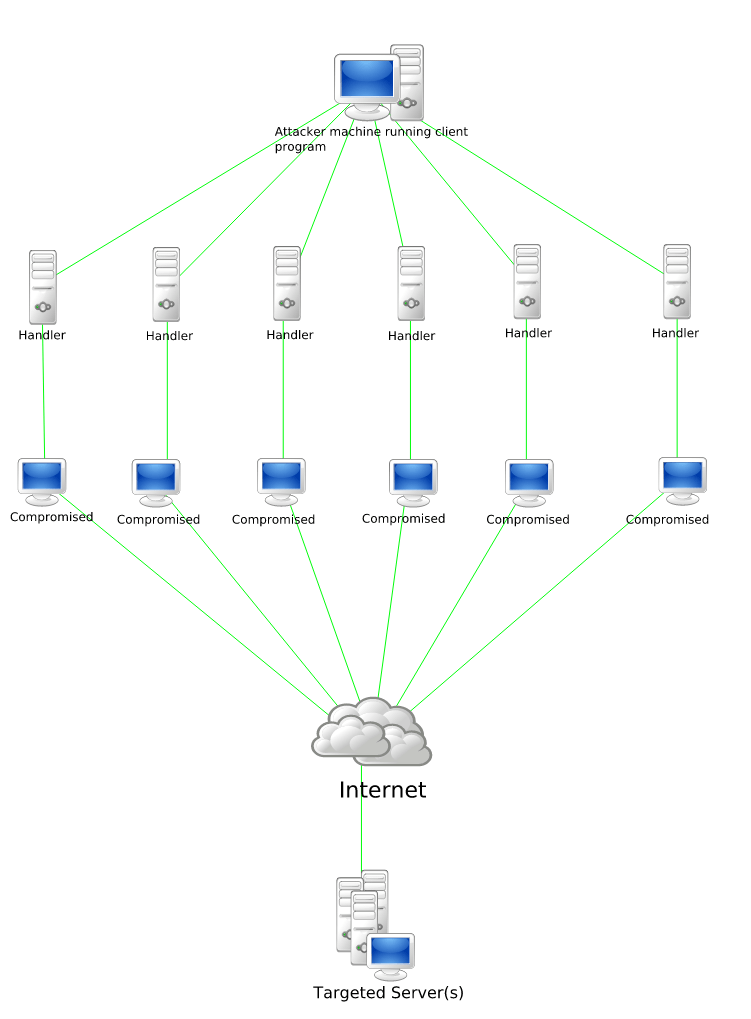
The difference between DoS and DDoS attack, therefore, lies in the number of attacks launched and in the number of “lines” exploited for the purpose: while in the first case you must defend from a single computer traffic source (for example a large number of emails coming at the same time), in the second case the attack is carried by more botnets coordinates on several levels (for example, a high number of web accesses coordinated with a large number of FTP connection attempts).
Therefore, a DDoS attack will need to average a shorter timeframe than a DoS attack to saturate the IT resources of the attacked system and also its deleterious effects usually will last longer.
Characteristics of a DDoS Attack
To saturate the resources of a computer system, hackers implement DDoS attacks simultaneously sending many requests for access to the same online resource. This allows, in short time, to make inaccessible a single website, server or an entire data center.
The various types of DDoS attack can be grouped into four main categories:
- Attacks on the TCP connection: the hacker tries to use all the available connections of the infrastructure network- a server or data center – so that it no longer reachable.
- Volumetric attacks: the objective of this type of attack is to completely saturate the transmission band available to a computer system so as to make impossible any form of communication.
- Fragmentation attacks: the data packets with access requests are sent in partial or incomplete, so as to lead the attack object computer system to use all of its resources – not only network but also computing – in an attempt to reconstruct the information digital receipt.
- Application attacks: instead of attacking the whole system, it attacks only one part – a program or application – critical to the IT ecosystem functioning. In this way, it triggers a process that makes unstable the entire infrastructure.
Learn More About DDoS Attacks
Incapsula has recently launched the world’s first-ever free training portal for DDoS protection.
It’s a training portal which offers a wide selection of free courses and challenging quizzes that test and improve your DDoS protection skills.
The courses cover the following topics:
- Introduction to DDoS
- Volumetric Attacks
- Protocol Attacks
- Application Level (Layer 7) Attacks
- Reflection Attacks
- Understanding Risks
- Mitigation Techniques
- DDoS Trends
The training is divided into Basic and Advanced levels so you can select the courses that best match your needs.
Get started by visiting the DDoSBootcamp here.
How to Defend Your Online Business Against a DDoS Attack
In the event that your online business is the subject of a DDoS attack you have very little chance to intervene. Only system administrators, in fact, will be able to mitigate the effects of an attempt to destabilize the computing environment under their control.
Various countermeasures, more or less effective, can be put in place:
Sink holing
In case of attack, this technique provides to divert all traffic to a dead end, so as to preserve the stability and full functionality of computing resources. It has the weakest point of making inaccessible the resource, either by diverting the good and bad traffic, but at least it saves the IT infrastructure – both hardware and software – from irreparable damage.
Routers and Firewalls
Before an attack hits the target, it is possible to stem the incoming traffic from non-essential protocols and invalid IP addresses by applying filters to the router and firewall. In case of more sophisticated attacks (attacks that use multiple levels of the communication protocol and at the same time many of guidelines attack), however, this technique is not very effective if not altogether useless.
Intrusion Detection Systems
Some software installed on servers and data center control systems are able to detect when the “legitimate” protocols and essential for the operation of the service are used to bring on an attack. If integrated with a firewall, it can block traffic to its malicious identified protocol and thwart the attack or at least minimize the effects.
Server
Proper configuration of the server and hosting services is one of the best antidotes to mitigate the effects of a DDoS attack. A system administrator, for example, may indicate which and how many resources can use a service like this and can respond to requests that come from the outside. In this way, in the case of an application attack, the effects would not be passed on the entire computerized system, but will simply knock out the only object of the attack software.
Overestimate Their Needs
It is, probably, the defensive technique that is most effective against a DDoS attack. Performing an overestimation of resources that will be needed in a given computer system, you will be able to cope without major problems, attacks that aim to saturate the bandwidth or processing power of a server or a data center. By utilizing a wide distribution of networks that extend into several states, for example, you will be able to survive a direct attack on one of the servers or a section of the network, simply by diverting the excess traffic to other “twin” computer servers even at great distances and not subject to attack.
Your Thoughts
This article introduced what are DDoS attacks and how you can improve the security and increase the protection of your online business.
Now, I’d like to hear more from you.
Have you ever heard of DDoS attacks?
Have you ever experienced one of them with your online business?
Please share your opinions in the comments below, thanks!
























Thanks for sharing all the information about DDoS attacks. It is really a criminal intent to attack external servers on the network and cause harm to the services.
Hey Erik,
I have heard a lot about DDoS attacks but never really understood what it meant. However, I now see that it is a big problem for online business owners. I should probably read some more about it and then take the quiz to see I am doing enough to protect my websites from such attacks.
Thanks for sharing the article!
Hi Erik,
Nice share indeed. This post helped me to learn about the DDOS. I have heard alot about this but never tried to learn about it. This post not only helped me to learn new things but also encouraged me to look for more info about DDOS. Will do some more research about DDOS.
Thanks for sharing.
Recent reports shows that DDOS attacks are happening more frequently than any other attack. It is always recommended to keep your site safe at any cost from such attacks. thank you for sharing detailed information about DDOS attacks.
Hi Erik,
This is good info. Many of us are not aware of a DDOS attack how vulnerable we can be if the worse happens. This post provides a lot of useful stuff on the subject. Will help a lot of people to better understand this and take preventive action.
Thanks for sharing and you have a wonderful day ahead!
hey thanks Erik for this info. it’s very helpful.